http POST bruteforce
25 July 2011
This post is a bit funny. It wouldn't have happened if I would not forget a password for this site. This actually never happened to me before: for 1-time sites I have easy 1-time passwords, and for something I am going to be using, I have strong passwords that I do remember. (UPD: not anymore; Troy Hunt made me understand that any password must be unique and very strong)
But for this site I have turned my imagination on, judging by posts dates, first two days I have remembered it, and now, few weeks later, I don't. I've spent like hour typing in passwords, failed.
"I'm a programmer, after all" — I thought, and wrote a program that would bruteforce the password for me. I had a set of "tokens" that I must have used when created a password, it made task much easier. I also didn't bothered with googling, implementing something fancy, fast, multithreading. Just a copy-paste from my other project, that have a site parsing part. Here it is:
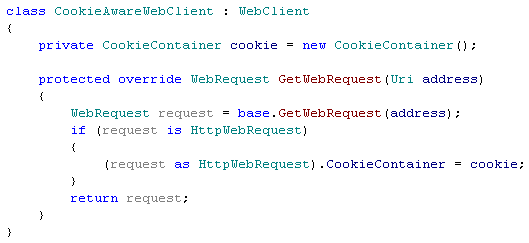
Code above allows you to be "logged in" with your WebClient via cookies. Code below is using CookieAwareWebClient to POST login-password, and then trying to download page, that is only available to users, that are logged in. There probably is some much better and faster way to understand, was login attempt successful or not (if you know better solution — please leave a comment), but this one was fast enough for me.
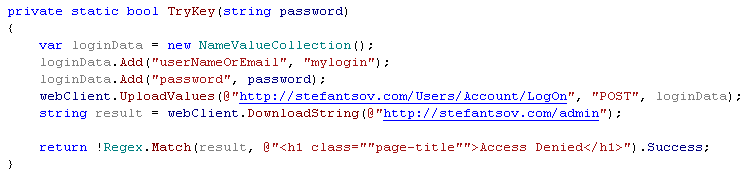
Now, once I have a list of possible password tokens:
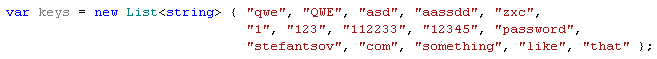
I just have to iterate over them and their combinations. Voilà!
(I figured out, if something is going to be slow and inefficient — that would be networking, retrieving /admin page in single thread. Not string concatenation and regexp; hence, no optimization here at all)
Links:
